What is a Computer Virus?
Computer virus is a software program, developed by a programmer that infects other programs. The problem created by viruses. includes :
- Destruction of file allocated table(FAT)
- Destroy part of program/data held on disc by creating bad sectors
- Erasing of specific program and data on discs
- Reduction of free space on disc
- Alter contents of fields in the file
- Formatting of discs or tracks on discs in a different way
- Suppress execution of RAM
Computer Virus & Its Types
Definition: A computer virus is a malicious software program loaded onto a user’s computer without the user’s knowledge and performs malicious actions.It can self-replicate, inserting itself onto other programs or files, infecting them in the process. Not all computer viruses are destructive though

Classification of Viruses
Viruses are classified on the basis of their mode of existence and there are three categories of viruses:
- Boot Infectors : A system infected by such virus will have the virus residing in a particular area of the disk rather in a program file. This virus get loaded soon after the Power on Self Test and control the system and remains in control at all times. Boot infectors create “bad sectors”.
- System Infectors : This category of virus deals with the components of the system itself. System infectors attach themselves to a file such as COMMAND.COM or other memory resident files and manipulate these files. System infectors differ from boot infectors that system infectors gain control after the computer is booted and infects a hard disk or bootable floppies which contain system files only.
- General Executable Program Infectors : This type of viruses are most dangerous virus. They attach themselves to a program files and can spread to almost any executable program in any system. This viruses change themselves to a program instruction. As a result , Whenever the program is executed, the virus gets loaded and executed first and then allows the original program to proceed.
Different Types of Virus
- Brain Virus : This is the first developed virus also known as Pakistani virus. It was developed by Pakistani brothers. The virus pops up screen saying “welcome to the Dungeon”. This virus is known to destroy data and are highly contiguous.
- Scores Virus : Score virus has a built in time trigger that activates at 2,3,4 and seven days after the disk has infected. Data files are not directly affected by this virus, but ensure of this virus requires deletion of all the files.
- Lehigh Virus : This virus originated at the Lehigh University computer centre. This virus stays in the stack space of COMMAND.COM . With the booting of a PC from an infected disk, the virus is spread through commands such as COPY, TYPE, DIR etc. The boot sector and FAT get ruined from this virus.
- Friday the 13th : This virus attack not only COMMAND.COM but also other executable files. When a .COM or .EXE file is executed for the first time after boosting the virus captures a specific interrupt and inserts its own code. It increases the .EXE and .COM file size cause the program to become too large in loaded into memory.
- SunnyVale Slug Virus: This virus display a message “Greeting from SunnyVale. can u find me ? “. And also modifies the COPY command resulting in deletion of files instead of copying.
- Raindrops Virus: This virus infects .COM files. It intercepts the load and execute the function of MS- DOS. It checks whether the file is .EXE or not. If the file is not an EXE file, the first three bytes of the file are replaced by a jump instruction at the end of the file . where it gets attached after encryption. This results in drpping or showering of characters on the screen like raindrops with sounds.
- Happy Birthday 30th: This virus gets activated on January 5th, If any of the program get executed , and will ask the user to type “Happy Birthday 30th”, It can destroy all the data on the disk.
- Key Logger: A key logger is a software program designed to record every key stroke on the machine. Its pupose is usually to allow the user of this tool to gain access to confidential information on the affected machine, such as a user’s password or other private data.
- Password Cracking: Password Cracking is the process of recovering password from data that has been stored in or transmitted by a computer system. A common approach is to repeatedly try guesses for the password.
- Packet Sniffer: A Packet Sniffer is an application that captures data packets, which can be used to capture passwords and other data in transmit over the network.
- Spoofing Attack ( Phishing ): A spoofing attack involves one program, or website successfully masquerading as another by falsifying data and thereby being treated as a trusted system by a user or another program. The pupose of this is usually to fool programs, systems, or users into revealing confidential information, such as user names and passwords, to the attacker.
- Rootkit: A Rootkit is designed to conceal the compromise of a computer’s security, and can represent any of a set of programs which work to subvert control of an operating system from its legitimate user to detect the presence of the intruder on the system by looking at process tables.
Common Security Breach Methods
- Worm : Like a virus, a WORM is also a self replicating program. The difference between a Virus and Worm is that a WORM does not create copies of itself on one system. It propagate through computer network. So it consumes system memory and network bandwidth.

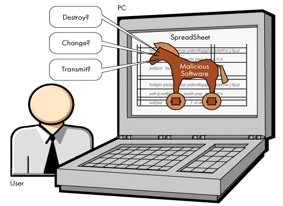
- Trojan horses : A Trojan horse is a program which seems to be doing one thing, but is actually doing another. A trojan horse can be used to set up a back door in a computer system such that the intruder can gain access access later.
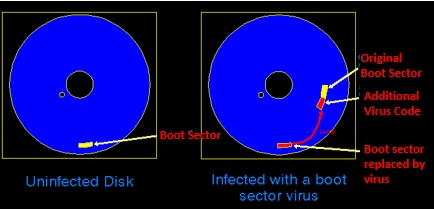
- Boot Sector Virus : A boot sector virus is a type of virus that infects the boot sector of floppy disks or the Master Boot Record(MBR) of hard disks(some infect the boot sector of the hard disk instead of the MBR). Eg . C Brain was the first boot sector virus created in 1986 in Lahore Pakistan.
- Macro Virus : A macro virus is a computer virus that infects the document files like MS. Word, Excel, Powerpoint etc. It causes sequence of actions to be performed automatically when the application is started or something else trigger it. A typical effect is the undesired insertion of some comic text at certain points when writing a line. A macro virus is often spread as an email virus. Eg, Melissa Virus spread in March 1999.
Spyware : These are the malicious(harmful) program which is installed into our system without your knowledge and collects the personal information without user permission.”Spyware” is mostly classified into four types : adware , system monitors, tracking cookies, and trojans.
Adware : These are the advertisement supporters which automatically renders for advertisement. These advertisement can be in the form of popup.
Malware : These are malicious program which includes computer virus, worm, trojan horse, spyware and adware,scareware and other malicious programs.
Important Points
- Creeper Virus was the first virus of world in ARPANET(Advanced Research Project Agency Network) in 1970.
- ELK Cloner was the first virus that act on PC in 1982.
- VIRUS stands for “Vital Information Resource under Seize”.
Thanks you and All the best!
You can join or visit at Facebook Page or Twitter for always keep in touch with further updates.
Read more articles….
| Computer Security | Hackers and Crackers – Types, Differences |
|---|---|
| Data Communication | What is Internet | Software Required To Access The Internet |
